About
Jok3r is a framework that aids penetration testers for network infrastructure and web security assessments. Its goal is to automate as much stuff as possible in order to quickly identify and exploit "low-hanging fruits" and "quick win" vulnerabilities on most common TCP/UDP services and most common web technologies (servers, CMS, languages...).
Do not re-invent the wheel. Combine the most useful hacking tools/scripts available out there from various sources, in an automatic way.
Automatically run security checks adapted to the targeted services. Reconnaissance, CVE lookup, vulnerability scanning, exploitation, bruteforce...
Store data related to targets in a local database. Keep track of all the results from security checks and continuously update the database.
Features
Compilation of 50+ open-source tools & scripts, from various sources.
Application packaged in a Docker image running Kali OS, available on Docker Hub.
All tools and dependencies installed, just pull the Docker image and run a fresh container.
Easily keep the whole toolbox up-to-date by running only one command.
Easily add/remove tools from a simple configuration file.
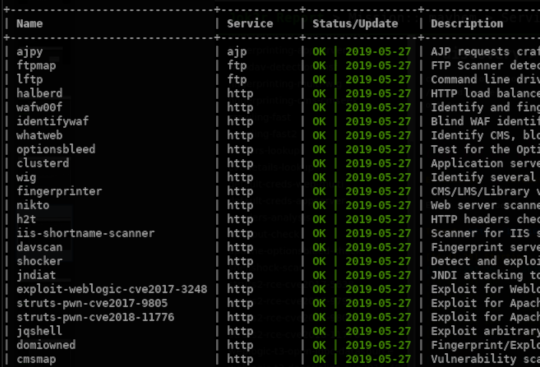
Target most common TCP/UDP services (HTTP, FTP, SSH, SMB, Oracle, MS-SQL, MySQL, PostgreSQL, VNC, etc.).
Each security check is performed by a tool from the toolbox. Attacks are performed by chaining security checks.
Security checks to run are selected and adapted according to the context of the target (i.e. detected technologies, credentials, vulnerabilities, etc.).
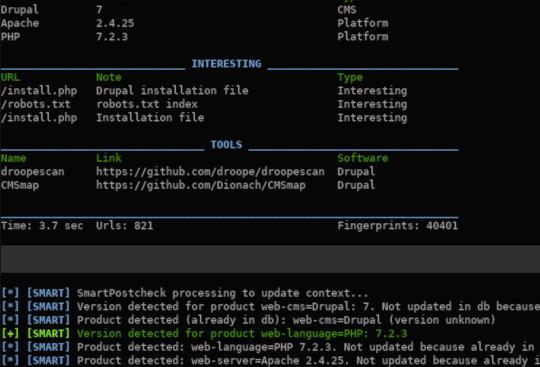
Automatic fingerprinting (product detection) of targeted services is performed.
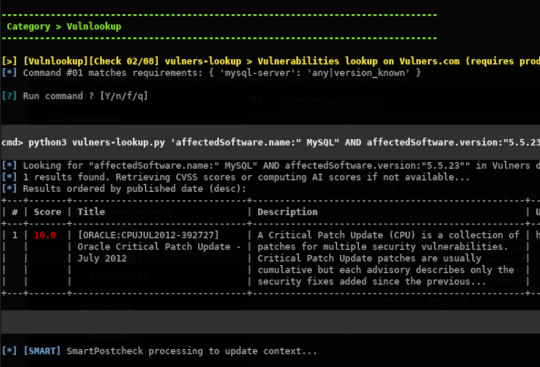
When product names and their versions are detected, a vulnerability lookup is performed on online CVE databases (using Vulners & CVE Details).
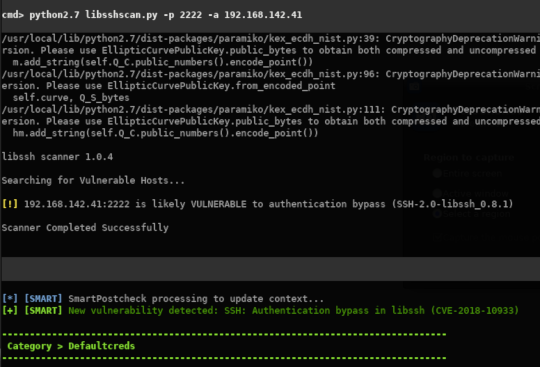
Automatically check for common vulnerabilities and attempt to perform some exploitations (auto-pwn).
Automatically check for default/common credentials on the service and perform dictionnary attack if necessary. Wordlists are optimized according to the targeted services.
Automatically perform some post-exploitation checks when valid credentials have been found.
More than 60 different security checks targeting HTTP supported for now.
Fingerprinting engine based on Wappalyzer is run prior to security checks, allowing to detect: Programming language, Framework, JS library, CMS, Web & Application Server.
Automatically scan and/or exploit most critical vulnerabilities (e.g. RCE) on web and application servers (e.g. JBoss, Tomcat, Weblogic, Websphere, Jenkins, etc.).
Automatically run vulnerability scanners on most common CMS (Wordpress, Drupal, Joomla, etc.).
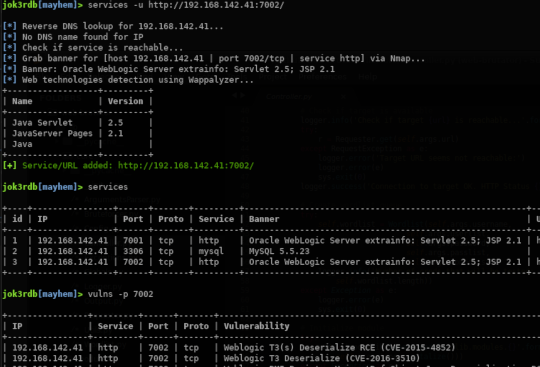
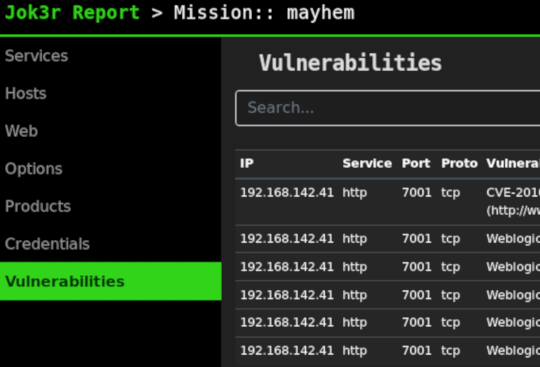
Data related to targets is organized by missions (workspaces) into a local Sqlite database that is kept updated during security testings.
Access the database through an interactive shell with several built-in commands.
Add targets to a mission either manually or by loading Nmap results.
All outputs from security checks, detected credentials and vulnerabilities are stored into the database and can be accessed easily.
Generate full HTML reports with targets summary, web screenshots and all results from security testing.
Architecture
General Architecture graph
Flowchart
Demo
Download
Jok3r is open-source. Contributions, ideas and bug reports are welcome !
Documentation
Full documentation writing is currently in progress... Stay tuned. In the meantime, you can check out the README.